
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Critical security considerations
Article for: Anyone considering using the Internet
Difficulty: Moderate
Importance: Very
Difficulty: Moderate
Importance: Very
A few breaches during the first three months this year:
- Ubiquity access to client's networks through their routers
- Parler
- Florida Water supply
- 2 million Nebraska medicine patients
- California DMV
- Kroger's had a third party cloud solutions firm comprise email address, email, home address, phone numbers, social security number and birthdate along with health insurance, medical history and prescriptions.
- Oxford University Lab
- T-Mobile
- Microsoft Exchange. Email and contacts exposed for millions of clients.
It is clear from this list that if you have information online, anywhere, it can be hacked and you can lose it.
The rule: Reduce your exposure
We need to be much more cognizant of the risks we are exposing ourselves to. Anything you put into Facebook or Instagram, or similar networks is potentially available to millions of hackers.
- If you put up a security system that is accessible over the Internet, then hackers could also access it.
- If your light bulbs talk to the Internet, expect that the Internet could talk to your light bulbs too.
- If you can access your router through the Internet, understand that someone on the Internet could also control it.
- If you send everything you type to Microsoft, Google or Apple, then someone there could read it. I wrote an article about this here.
- If you can control your thermostat over the Internet, it is possible others can as well.
- If your pharmacy or doctors' office has your information online, it can be hacked.
I am not suggesting that you do not do these things or hide under your bed, but I suggest that you consider this when you choose to do these things. I was a believer in the Ubiquity routers until they exposed all their clients' networks and then seemingly covered it up. Be watchful. Limit your exposure.
My Tips
- I do not connect my thermostat to the Internet.
- Setup a guest network and connect devices like thermostats, Roku TV or other IOT (Internet of Things) devices to that network, not your network. Avoid the IOT when possible.
- Use a mobile device keyboard that keeps your typing local and does not send it to Apple or Google.
- Stop everything you type in Windows 10 from being sent to Microsoft. You do this by: Settings > Privacy > Inking and typing personalization. Turn it off. This really irritates me.
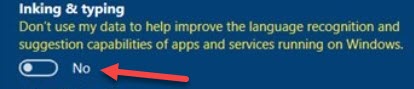
The only potential reason to make this cloud based is so you can share your information across multiple computers you use. Computers are fast and powerful enough so that they can process this information locally, without needing to send it to Microsoft. They could adapt to you and learn without ever allowing the information to leave your computer. Fleksy keyboard does just than on mobile devices. - Avoid all Internet connected devices if possible. When you can, keep your information and processing local. Use cloud computing only when there are overwhelming advantages.
- When you require a cloud based mobile security system or similar system, go with a vendor that does rapid and frequent security updates. Don't cheap out.
- If possible, do not allow cloud access to your router. If you need cloud access, have it setup by a professional.
- Often, cloud access allows computer consultants to manage and protect your systems. Normally, this is very useful, but understand, the consultants protect you, but allowing them in also creates a risk. If the consultant gets hacked, those hackers could have access to you too.
- Do not give information to online vendors that they don’t need.
- Lie. I'm very much an honesty freak, but feel no need to be honest about information the online vendor does not need.
- Always lie when asked for security questions. For example, you can answer the question "what city were you born in?" with 895. Never give a correct answer to these questions. Consider these questions to be like passwords. Use nothing attackers could find out. Always record your questions and answers in the notes of your password safe. Then copy and paste them into the website.
- The one place I supply correct information is on user forums. I always sign in with my real name. Maybe it'll bring me business as I help people, and maybe using my actual name will stop me from acting like a jerk.
- Never use the same password in two places. Use a password safe and long random passwords for every site.
Further reading
- Worst Data Breaches and Cyber Attacks of 2021 so far
Date: June 2021

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.