
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Online Credit card skimmers
How they work
Article for: People who buy online
Difficulty: Easy
Importance: Important safety tips plus information
Difficulty: Easy
Importance: Important safety tips plus information
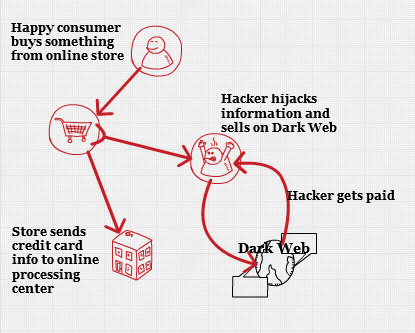
The frequency of online credit card skimmers, also known as digital card skimmers has surged. Currently, this is the biggest online threat, replacing ransomware and cryptomining. Hackers breached thousands of online retailers in 2018, including Ticket Master, NewEgg, Sotheby's and British Airways. Symantec claims they blocked over a million attempts against the sites they protect in just the last three months of 2018.
They implant these skimmers by direct attack against the site, but also indirectly through the victim's supply chain. They make the supply chain attacks against the victim by compromising their security firm, hardware or software vendor. The skimmer can get installed using the update mechanisms or infected computers of these vendors. There are also attacks against the software makers of the digital shopping carts online stores use.
According to recent Thales eSecurity research, 50% of all medium and large online retailers admit someone hacked them.
How they cash in
Once the hackers have a few thousand credit cards, including names, addresses, and even security codes, they sell them on the dark web. Prices range from $2 to $8 each, so 10,000 records can bring in around $50,000. Normally, they remove those cards from inventory and do not resell them. Hackers develop good or bad reputations depending on the quality and exclusiveness of the information.
The buyers clone the cards, making actual physical cards. They use these in brick and mortar stores. The cloned cards scan just like the original card.
What can I do about it?
You can't do much to protect yourself. You are going to the correct site. There is no way to know if someone else is getting the credit card information you put in. It does not help to use their special app. They can still steal your information. But, some things can help mitigate the problem:
- Obviously, you want to check your credit card use. The more often the better.
- Reconcile your accounts every month.
- Sign up for alerts from your bank so you get a notice whenever your card is used. .
- Check into virtual credit cards from your card company. Each bank is different, but basically they will create a virtual card for any online store you use. That virtual card will be linked to your real one, but the account number will only be for that store. The number cannot be used elsewhere. When you get a new credit card, your virtual numbers will transfer automatically to the new card. You'll have an extension in your browser that will pop up when you are asked for a payment and you can select the appropriate card and it will fill in the card information for you. See how your bank's browser app is rated before you jump in.
- I leave some money in my PayPal account and use the balance to make purchases from smaller vendors. This account is not linked to a credit card, but to a small bank account that does not have overdraft protection. This might help, or maybe it's just a waste of time.
Further reading:
- Bleeping Computer article
Date: June 2019

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.