
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Our connected world
 "To light a candle is to cast a shadow...â€
"To light a candle is to cast a shadow...â€â€• Ursula K. Le Guin, A Wizard of Earthsea
"The very same phenomenon which is appearing to be good now, may appear to be bad tomorrow."
Swami Vivekananda
More and better devices are providing more and better connectivity to the outside world. My router connects me to the entire Internet and to my clients for remote support. I can pop into a client computer and solve an issue for them in just a few minutes, instead of driving to their office, parking, helping them and returning; requiring perhaps an hour. It connects me to shopping sites and bookstores. I download audio podcasts and audiobooks from Audible. I stream my TV viewing through a Roku box and do not pay for TV cable service. These are wonderful benefits. But along with the benefits are innumerable perils.
The VPNFilter botnet took control of over 500,000 routers and NAS boxes. Other malware have compromised computers, servers, security cameras, thermostats, doorbells, baby cams, printers, phones, refrigerators, TV sets and tablets. Once compromised they can mine for crypto-currency using your resources including your electricity, send out spam, attack and bring down websites with your devices, encrypt people's files and demand ransom, and propagate other malicious scams. Attacks bringing down respectable websites increased over 90% from 2016 to 2017 because of all the connected things we now have.
Some recent IoT hacks
- Cloud Pet toys were pulled from stores
- Hacked Security Cameras
- Mirai botnet which attacked printers, security cameras, and home routers. Infected 2.5 million devices.
- Thermostats held for ransom. Want your house held at 99 degrees?
- Smart door locks
Every time you connect anything to the Internet, even a light bulb, you are connecting a computer to the Internet. Researchers and malicious parties study those computers and find security flaws which they can use to compromise the devices. If it touches the Internet, it will become a target for governments and other miscreants.
How Botnets work
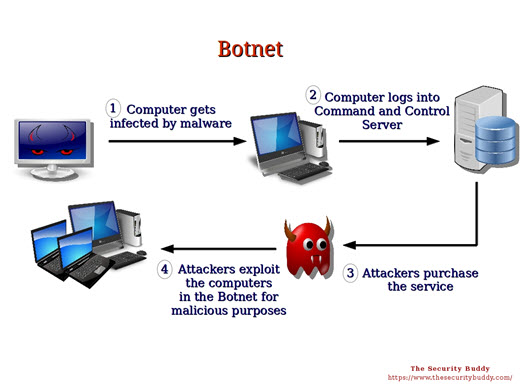
- Some clever people figure out how to infect printers, or doorbells, or computers or routers; any connected device.
- Once infected that device logs into a command-and-control computer to get more malware and instructions for infecting more devices.
- When the Botnet owner has thousands of infected devices under his control, he rents out the Botnet to people who use it to send out spam, attack unwanted sites, steal information or do crypto mining.
- They then use the infected devices for some period of time to do the bidding of their masters.
Why it remains a problem
By buying the cheapest devices, many people are not paying the vendors to keep up on the latest security problems and paying their programmers and security teams to fix the problems that surface. They are not paying for the company to include a system of constant research and updating and patching these computers to prevent them from being taken over.Companies realize that making their products secure will cost them money and keeping them secure after the sale, will add even more costs. If customers do not demand security, then they will be pricing themselves out of the market.
Router Examples
The cheap routerI recently updated a low cost router from a company that constantly manages to offer a very good product for less. The update was already 5 months old and didn't include patches for vulnerabilities that were revealed last month. I needed to go to their website and find the correct firmware update matching both the model and version of the product. After downloading the firmware I needed to unzip it and then apply the patch. The patch wiped out all their current settings so I needed to reload their security settings, passwords and so forth. I also needed to know the default user name and password to login so I could reconfigure the router.
The mid-priced product
Updating a mid priced router was much easier. Their patches are more frequent and include fixes for the big flaws revealed last month. I clicked on their warning that I needed to update and it downloaded and installed the update for me without losing any settings.
The high-priced product
This router has security patches frequently. It recognizes the need and updates all by itself without my intervention.
My IoT Rules
- Avoid the devices when possible. Be a little less connected. Think three times before you connect your garage door or doorbell to the Internet. Then don't do it.
- With devices you need, choose as little Internet access as possible. Turn off their cool features! For example, your printer may not need to have Internet access. Your router probably doesn't need external remote access or Universal Plug and Play. Turn off the fancy features you do not need.
- Do not buy any IoT product that does not have a good record of frequent security patches. You need to pay a company to maintain their product and keep it secure as new threats are discovered. Check the company's record and system for patching their product.
- Connect IOT devices to a guest network, not your main network.
- Change the default credentials (user name and password).
- Update your firmware frequently.
- Avoid Peer-to-Peer (P2P) options.
Further reading
Top 10 IoT threats - Remote recording, spam, Ransomware. What would you pay to get control of your garage door opener back, or your coffee pot, or thermostat?Date: July 2018

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.