
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Podesta's Mistakes - Let me count the ways
While it is certainly possible that Russia hacked John Podesta's email, I am not sure and for my purposes it doesn't matter. The attack appears to be so simple and poorly executed, that any professional would be ashamed of it and could not expect a person of normal intelligence to fall for it. On the other hand, it worked, and many similar ones worked as well. Similar techniques were used to hack Colin Powell's email, and numerous celebrities Apple iCloud accounts. A high school student hacked Director of National Intelligence James Clapper's email and CIA Director John Brennan's AOL account.
So, I will examine what we know about it and the mistakes that were made.
Podesta had a Gmail account and received an email that told him his password was stolen and his account had a false sign in. He should click on a link and change his password. This email was forwarded to some IT guy for the Clinton campaign who said, wow, do it right away, this is legit. This was what the email looked like.
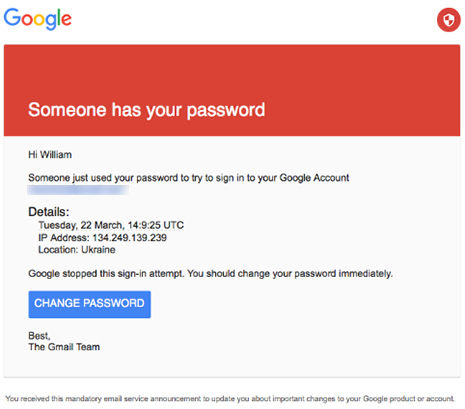
If he had hovered over the link to change his password, as I've recommended here, he would have noticed that it went to a Bitly link which hides where the link is actually going. Bit.ly shortens long addresses. While this is often useful, it is never used in a situation where security and authentication is important.The idea that Google would hide where your link was going to shorten it is ridiculous.
The site it went to was not Google.com but com-securitysettingpage.tk. TK is Tokelau, a territory of New Zealand. However, they obscured the address further by prefixing the domain with myaccount.google so it read myaccount.google.com-securitysettingpage.tk and further obfuscated it by adding /security/signinoptions/password? and more. Making it difficult to interpret.
If they had checked the From: address, they also could have spotted the fake.
So, Podesta violated lots of simple rules.
- Never click on the link. If you want to call or login, never ever do it from a link or emailed phone number. Call the number you have or go to the login for your account from your password safe or bookmarks. Not from something sent to you by email!
- Hover over any link and check it out. If a link is supposed to be from Google, it will not link to www.badguysareus or google.email.badguysareus
- Check the address bar on the website. If he'd looked he would have seen it wasn't Google.com
- Podesta used a very weak password: Runner4567 revealing a complete lack of fundamental security understanding
- Podesta used the same password on multiple accounts, so when he lost one, he lost control of multiple accounts
From an administrative viewpoint:
- Fire the IT guy. He should have spotted the fake.
- Train the staff. No one should be as untrained as Podesta and in control of sensitive information. This was very negligent.
How does this hack work?
You get a notification that seems to be from your credit card company that your statement is ready, with a link to get it. Never ever click that link. It would be too easy for a miscreant to copy that email message and make one exactly like it but with a different end point. Once you login to their fake copy website, they send your credentials to the bank and forward the bank information back to you. You never know anything is wrong. Everything works, just a tiny bit slower. You get your statement and they now have control of your account. They can set up a transfer to an account they own. They could send out a hundred thousand copies, and if they captured only 1% they would have captured 1,000 bank accounts.In this case, they had full access for months to John Podesta's email account.
More information
- Business insider
- More in-depth article from Motherboard.vice.com
Date: November 2016

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.