
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Testing Your Router
 Your router is a wall between your computer(s) and the wild world of the global Internet. Lots of bad guys hang out on the Internet and it is the job of your router to provide the first line of protection. If an unprotected computer is placed on the Internet, it will be infected and taken over in less than 5 minutes. The biggest problem will be all the viruses fighting each other for control. Think cesspool.
Your router is a wall between your computer(s) and the wild world of the global Internet. Lots of bad guys hang out on the Internet and it is the job of your router to provide the first line of protection. If an unprotected computer is placed on the Internet, it will be infected and taken over in less than 5 minutes. The biggest problem will be all the viruses fighting each other for control. Think cesspool. Windows has a firewall that provides a second line of protection. But, still, it makes sense to check whether your router is giving you the control it should. A well respected and safe test for your router comes from Gibson Research Corporation's Shields UP!
UPnP: Universal Plug and Play
UPnP is a protocol that was developed for small workgroups or home offices. The idea was that when a network printer or scanner was added to the network it should be able to install on all the computers in that network. Since everyone was in the same office this was considered by its originators to be reasonable. They didn't even build in any way to authenticate that the device came from a trusted source or was what it claimed to be. Naturally, miscreants immediately began designing viruses that would say to your computer:"Hi, I'm a new printer on your network, install me ;)"I immediately began turning off this functionality in all computers I was responsible for.
But, wait, there's more. In 2011 security researchers found that you could exploit the UPnP protocol to attack networks from outside the network through the Internet. Routers began opening themselves up to UPnP calls to make it easier for Internet servers to send messages and controls through your router and not get blocked. This is useful for children to play Internet games, or for people to manage webcams, printers surveillance cameras and more without knowing how to punch a hole for the device in their router.
Of course, since there is no authentication, these holes are easily exploited, so it is best to turn off your router's UPnP access. Something I do when setting up a router.
The first test that you should do is the UPnP test. Ten packets are sent to see if they can get in through the UPnP protocol.
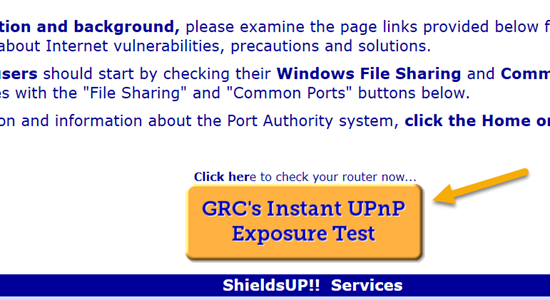
When you run this test you should get a result that looks like this:
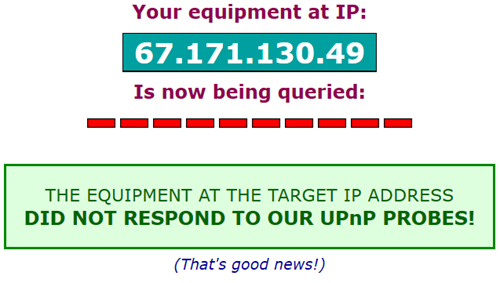
Your test will be followed by an explanation of its meaning.
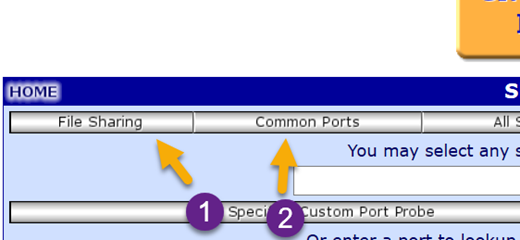
After you have done that, go back and start the testing again. This time go below the UPnP test and run the Filesharing test and then the Common Ports test.
Open File Sharing
The filesharing test will look at Port 139 to see if your computer is acting as a server and will also test whether NetBios is accessible from the Web. If so, it is possible that outsiders could gain access to your files. Open Port Testing
In all of these tests, GRC sends requests to your computer for information. It will report one of the following three results:- Exposed or Open: Yikes. Your computer is asking this stranger what it wants. This is bad. You are exposed.
- Rejected or Closed: Your computer says it will not talk to anyone. It is rejecting the requests. This is good.
- Stealth: Your computer refuses to even acknowledge that it exists. It is not refusing the requests because it refuses to acknowledge that it even received them. This is VERY GOOD. Some consider it bad manners, not acknowledging the request, but I consider it a small bit of added security.
The Common Ports test results should look something like this:
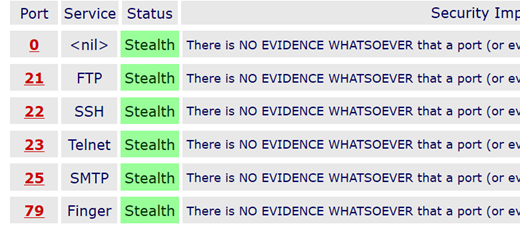
If your computer is showing closed instead of Stealth, that is just fine. Don't worry about it. The full port test takes quite a while as packets are sent to 1056 ports. You can do that if you like.
Further Reading
- Here is an article about how to setup your router
- Here is a form to use to help setup your router
- Here are instructions for using the form.
Date: October 2016

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.