
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe

Two New Security Threats
Two new types of security threats have appeared and they are dangerous.
Cross site request forgery.
When you log onto your bank or credit card or Amazon account you enter using your password. Most sites give you a session cookie so they recognize you as you move from page to page. If, instead of logging out you simply close the tab or leave the tab open while you do other things, you can be exposed.
The bad guys are sending out Emails which contain an invisible graphic which downloads a Javascript and runs it. The villain hopes you are using that bank or Paypal or whatever, and sends a change of address or new password request, or makes a purchase. The originating site sees you come back through your browser and continue your activity, so it accepts it.
If they send out 100,000 emails and are able to access 0.1% of them to compromise checking accounts, credit cards or amazon accounts, then they could get rich.
This problem can be handled fairly easily if the website protects their forms with a hidden key. However, many do not.
How to protect yourself:
- Always log out of anywhere you log into as soon as you are done.
- Use the Buttons! thunderbird add-on to control html email.
- Use Thunderbird to avoid loading images unless specifically chosen.
- If not using Buttons!, disable the preview pane.
- Use Mailwasher if you get lots of spam to pre-screen in text mode.
Click Jacking
Click jacking can occur when something invisible is underneath an object you click on in a website. This can cause a click to the hidden object. So, if you have your browser setup to automatically log you into your account when you go to a site, they could then enter an address change and have the ok button hidden behind the site.
NoScript protects you from click jacking. Here is an example of a warning that occurred when I visited ESPN.
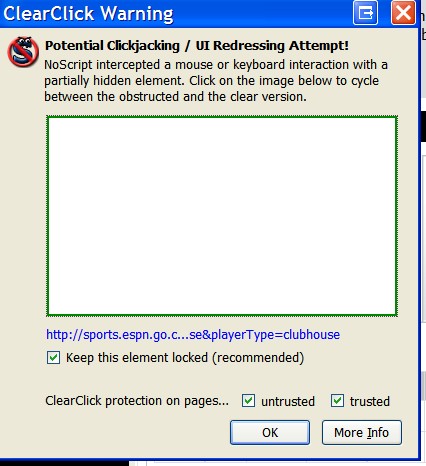
Unfortunately, some sites use the technique of hidden elements of legitimate purposes, so NoScript gives false positives, alerting you of danger when there is none. Even without NoScript, you can protect yourself by NEVER having automatic login enabled to a site that contains private or valuable information.

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.