
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Certificate Revocation
Sites use certificates to establish a secure connection to your computer and to verify that they are who they claim to be. Only the USBank can have a USBank certificate and it is signed and certified by a Certificate Authority. But sometimes, these certificates get lost or stolen or something happens where that is a possibility. When that happens, the site revokes its certificate.So, how does a browser know whether the certificate it receives is current or has been revoked? The standard way is to use the Online Certificate Status Protocol to check with master servers to determine whether a certificate was revoked. After the Heartbleed vulnerability, tens of thousands of sites revoked their certificates and got new ones. This put a lot of pressure on those servers as so many new certificates had been revoked.
Both Mozilla with Firefox and Google with Chrome, worried that if it checked and the authority didn't respond quickly it could slow down the Internet experience. So Firefox decided that if the check failed to get an answer quickly, it would assume the certificate was valid. The problem with this strategy, is that if someone was intercepting your traffic and could insert a phony certificate, then they could make the certificate check time out. This means the entire check is worthless.
So about four months ago I changed the default to assume it is invalid if it is not verified as valid. Firefox will check for 10 seconds if it is set to consider the certificate invalid if it fails. In the entire 4 months I have never had a failure. Other consultants also performed this check and they too never had a problem. So now, I can recommend this.
Change the Firefox Default
To change the option to assume invalid if the connection check fails, to to Options> Advanced > Certificates and uncheck When an OCSP server connection fails...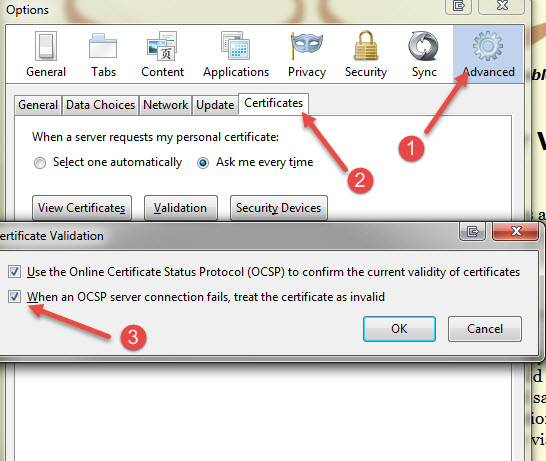
Chrome
For this and other reasons, Google decided in 2012 to not have Chrome use the Online Certificate Status Protocol for certificate revocation on non-EV certificates. (EV or Extended Validation certificates are more expensive certificates with more stringent buyer verification and browser behavior rules.) Instead, Google uses their Chrome update mechanism to send batches of serial numbers of revoked certificates which it gathers by crawling some Certificate Authorities.Chrome maintains a list of about 24,000 revoked certificates, which it updates frequently and checks against this local list. Essentially, they keep up with the revocations of many of the main certificate authorities. This makes the browser faster. Sadly, there are about 2,000,000 revoked certificates, so they simply are not giving their users the protection I wish they had, and to my knowledge there is no fix.
Date: October 2014

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.