
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Because of the seriousness and the panic surrounding this vulnerability, I've decided to send out an emergency alert to my email newsletter clients
regarding the Heartbleed vulnerability.
Heartbleed Vulnerability. What is it? What to do?
What is it?
A very commonly used secure connection protocol has had a flaw for years that was recently discovered and made public. The flaw allows a miscreant to jump into the server using that protocol and capture about 25 pages of information. They can keep jumping in and grabbing lots of 25 page clumps.So what?
If your email and password was in one of those clumps, then they have your login credentials. Also, if the certificate code that verifies that the host is in the clump, then they can impersonate the host server.Why is it so bad?
On Monday the exploit was made public. Before that, major players like Google and Yahoo didn't even know about it. Normally, the flaws are revealed to the people who can fix them before being made public, so there is time to fix it. This time, the miscreants found out about it at the same time as the server hosts. Later on Monday, the code was posted so that any miscreant could search for servers with the vulnerability and exploit it before the legitimate players had time to patch it.What to do?
- Change your password for sites that indicate they were vulnerable, but are now patched: this means on your computers, tablets and phones! Use the lists below, the links to lists or the test sites links below.
- Make sure your browser checks for certificate revocation.
The Biggest danger
We will need to change some passwords and do some other things, but the biggest problem will probably come from the panic and miscreants taking advantage of the panic. I expect a deluge of miscreant attacks on scared users:- Emails that seem to be from Google or Yahoo or Facebook asking you to change your password and providing a convenient link. DO NOT PRESS IT! Once again, Do not sign in from a link provided in an email.
- Programs offered to update, add to, or improve your security. "Just install this program and we'll protect you." Never install a program from an email or advertisement. Go looking for it or something like it independently. See what comes up from legitimate sources. See how users and experts respond to it. Call me and ask.
- Phone calls from fake Microsoft or Comcast representatives who will offer to help you.
- They will figure out other things I don't think of, so be super vigilant.
Be paranoid. Be really really paranoid about these kinds of solicitations.
Who is vulnerable, A Short list for my clients: Change your passwords on these sites
- Yahoo email
- Gmail (Google, they say you don't need to change your password. Do it anyway.)
- Your own website (probably)
- Youtube
- Godaddy
- TurboTax / Intuit
Who is not vulnerable, A short list for my clients: You don't need to change these passwords
- Linked In
- Amazon Shopping
- Hotmail
- AOL
- Ebay
- Paypal
- Evernote
- Lastpass
- Spideroak
- ChaosHost
- MySecureBackup
- I have not seen ANY bank, credit card company or Investment firm that is vulnerable
Good Lists of sites vulnerable and not:
- http://mashable.com/2014/04/09/heartbleed-bug-websites-affected/?utm_campaign=Feed%3A+Mashable+%28Mashable%29&utm_cid=Mash-Prod-RSS-Feedburner-All-Partial&utm_medium=feed&utm_source=feedburner&utm_content=Google+Feedfetcher
- https://www.yahoo.com/tech/the-heartbleed-aftermath-drags-on-what-passwords-you-82296501283.html
- http://money.cnn.com/2014/04/10/technology/security/heartbleed-passwords/index.html?hpt=hp_t3
Test Sites
You can enter a domain and get results regarding its current and past vulnerability- http://filippo.io/Heartbleed/
- https://lastpass.com/heartbleed/
- https://www.ssllabs.com/ssltest/
- http://heartbleed.criticalwatch.com/
Checking your browser
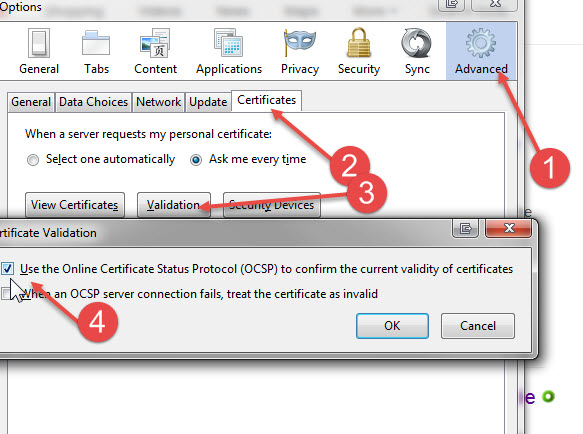
Because the Site SSL certificates could have been compromised, it is potentially possible that a villainous site could impersonate your vendor's credentials and fool you if they could get you onto their site. So, virtually everyone of them is revoking their current credentials and getting new ones. But this is only helpful if your browser checks. Here is how to make sure Firefox and Chrome check:Firefox:
Options/ Advanced/ Certificates/ Validation - Make sure Use online Certificate Status ... is checked
Chrome
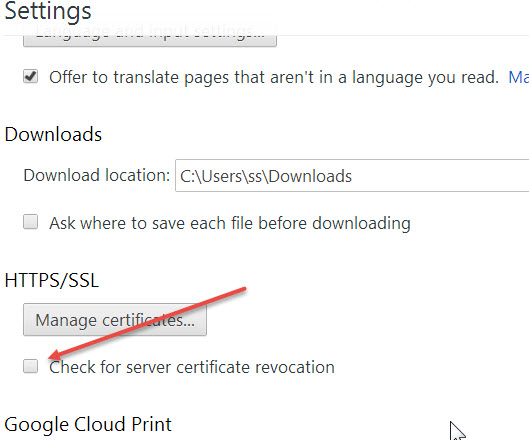
- The three lines on the upper right lead to Settings.
- At the bottom Click "Show advanced settings"
- Go down to check for server certificate revocation and make sure it is checked
Date: May 2014

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.