
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Catastrophes can happen. Use quality passwords.
Preview:
Re-using passwords can result in catastrophes. Using weak passwords or reusing them can lead to losing your Email account, then more accounts can follow, spelling real problems and a serious mess.
A client called me. He'd lost control of his email, his Microsoft account, his Facebook account, perhaps more. What to do? What happened?
The first issue was his email account. A hacker had gained control of it. Once that happens, a person is in deep trouble. There are so many sites that if you forget your password, they'll just send you a reset password email. So a hacker who has your email login can go to your accounts and claim to have forgotten his password. Then reset links are sent to the hacked email account, and he resets many of your accounts. You are then locked out of them.
I helped him regain control of his email. We created a real password for it (30 random characters), and used his cell phone for the 2nd factor authentication. Once we had that, we turned to his Microsoft account, which was also controlled by the hacker. We regained control of that as well, but it wasn't easy.
Finally, I turned to his Facebook account. Now, 10 days later, we still do not have control. I've given up. A miscreant is running his Facebook account. He can do nothing about it. You see, the hacker, after gaining control, added two-factor authentication with an authenticator application. This is good protection. It will even stop the real owner of an account from recovering control after his or her account is hacked! It is much better than email or SMS message protection. Without having the authenticator application app key, we cannot access the account or change the password.
Facebook has an account recovery procedure, but if the hacker adds an authenticator app as the second factor, there is nothing we as users can do. We uploaded his photo ID, and they verified the ID is the ID of the account owner. Then they requested the One-time-code from the authenticator app, which we cannot give it. This is a well-known and documented problem. Many users have reported it. But there is no way to contact Facebook and talk to someone. They do not have a user forum that functions or a chat. If the hacker added 2FA using an authenticator app, then the owner is locked out and cannot regain control. This is an issue with a free service that has 3 billion active users. Even though the authenticator app was added AFTER the hack, Facebook's recovery procedure does not work.
How did this happen, and how is it prevented?

These kinds of problems occur when people reuse the same password in multiple places or use similar passwords. For example, if you used sweetkitten2, then used sweetkitten or sweetkitten22 or sweetkitten21 it can be disastrous. My guess is that some site somewhere lost his email address and password. Then a hacker, from somewhere on Earth, tried various similar passwords for his email. Once he broke that, he changed the password, locking my client out, that then pursued other accounts like Facebook and Microsoft. Many databases exist on the dark web of username/password combinations. One of them has over 22 billion entries. You are not safe using any password that has ever been used by anyone, let alone by yourself.
The password rules are simple.
- No password less than 20 characters long.
- Passwords should normally be random collections of characters.
- Passwords should include at least 3 of the 4 character types, symbols, numerals, upper case and lower case letters.
- No password should ever appear anywhere. Nothing that is in any dictionary or Wikipedia or anywhere else. Nothing that is a combination of two or three words that appear anywhere. No phrase that appears anywhere.
Finally, No password you can easily type. The only two exceptions to this rule are:
- The password to your password safe, and
- Your Google account (or Apple account)
The reason that Google and Apple need to be typeable, is that when you get a new phone or tablet, you may have to type that password on that small screen. Still, you can augment the base password with random stuff. You can also spend some time typing once every few years.
You must use a Password Safe! Let it generate random passwords for you.
Finding weak and duplicate passwords in KeePass and Bitwarden
Both password managers I recommend provide assistance in finding your weak passwords, so you can change them.
KeePass
Under the Find menu, you'll see four optional reports:
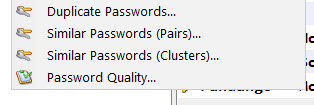
These are useful for weeding out your weak passwords or any duplicates you may have.
Bitwarden
For $10/year, Bitwarden offers a premium account which provides many valuable benefits, including security reports. I recommend it. If you log into your Bitwarden Premium account online, you'll have an option for reports in the left-hand menu. Included in these reports are:
- Exposed passwords — Any password that was ever used anywhere by anyone is a vulnerability.
- Reused passwords
- Weak passwords
- Data breach — Checking for sites with your password which were breached and exposed.
Date: February 2025

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.