
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Basic File Encryption
Preview:
This is the first of a two-part series on encryption. I explain basic encryption, file encryption, and End-to-End encryption. I stress the importance of understanding, who has the keys.
Symmetric crypto or private key cryptography
The simplest example of a symmetric key is a decoder ring. An outside set of letters and an inside set of other letters or numerals. You simply know the offset and have matching rings, and you can choose the letters on one ring for your message and write the matching letters from the other ring.
A decoding strip as shown below could work like this. To encode use the top for you message. To decode use the bottom. So "I have a cat." becomes: TASL4PALANL2
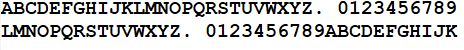
To decode, we'd take the bottom letters and use the top ones. So the T becomes an I, the A becomes a space, and the S is an H and so forth.
If two people have the same decoder rings or strips, and know the off-set, they can write secret messages to each other.
How it works now
Since those secret decoder rings weren't very secure (sorry Captain Midnight), we have developed much better systems. This is how a program creates proper encryption keys.Step 1: Create a key
- The user inputs a password. For this to be secure, it must be a combination of characters which has never been used before.
- The program salts the password. This means that the program adds something to the password that changes for each user. This prevents an attacker from creating a table of passwords and their transformed values as keys. Now, even the same password, would be different for two different users.
- The program doing the encryption transforms the password into a secure key. It uses a special tested formula designed to provide a seemingly random fixed length key, usually 256 bits. For example, my Bitwarden password manager uses the Password-Based Key Derivation Function 2 (PBKDF2) formula.
- Then the program runs that key through its formula and transforms it again and again, thousands or millions of times. This forces anyone testing different possible passwords to work thousands or millions of times harder. For example, Bitwarden repeats the transformation 600,000 times by default. I always recommend changing the default, but remember, if you set it too high, it will take longer for programs to log in. For example, if a password could be broken in one day with a single iteration, 600,000 iterations would require over 1,600 years (600,000 days). However, it'll take your computer less than a second to do the 600,000 iterations just once.
- The result, after iterations, is the output key, actually used for the encryption. Your password is used to produce the key, not to do the encryption.
Step 2: Encrypt the file
- This encryption key cannot be reversed. There is no known way, if you have the key, to determine the password.
- The key runs through another formula to encrypt the file.
- The same key is used to decrypt the file.
The Critical Factors to understand
- If a password safe is encrypted properly, then only by inputting the password and having the properly configured algorithm, salt, and iterations can the file be recovered. If you lose your KeePass or Bitwarden password, then you will lose all your passwords. The file cannot be recovered.
- If someone else has your password, then they can see your file.
- If you can reset your password, then whoever lets you reset it, has your key. The file must be decrypted, then the new password is used to create a new key that is used to encrypt the old file.
End-to-End Encryption
If you don't want someone else to have your password or keys and be able to read your files, then you'll need E2EE or End-to-End Encryption. This means that your program encrypts the information, then sends the already encrypted package to the recipient. The key never leaves your control. It is never sent. The recipient has no access to the key and cannot recover your information or help you if you lose your key.Many companies brag that your information is sent encrypted, or encrypted in transit. This only means that your computer and the recipient computer (perhaps Google for Gmail), agree on a key to use for the transport. Once the data arrives, it may or may not be encrypted at rest. Even if it is, the employees of the company holding your data can access it.
However, with true E2EE, like Bitwarden Password manager has, or Spideroak One Backup has, the data is encrypted on your computer and you have the key. Neither Spideroak nor Bitwarden employees can see it.
Next Month
- Next month, I'll explain asymmetrical encryption or public private key encryption. This exciting technology allows you to exchange information with someone else, like your bank. It lets you and the bank:
- Authenticate your identities
- Hide the information from everyone else, even if other people are watching the entire exchange!
- Agree on a symmetric key to use for encrypting your important information. No one else will know that key.
- Know that nothing in the message was changed.
Date: December 2024

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.