
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

KeePass Can Replace Authy Desktop
Preview:
Twilio's Authy desktop authentication app is being discontinued. Here are my recommendations to replace it. I've included a tutorial on using KeePass for your Time-based One-Time Password authenticator.
Twilio is killing off Authy for the desktop, so if you were using it, here are two recommended replacements. You could use Windows Authenticator, but I don't trust Microsoft with my data, so I won't recommend it. There is a movement away from using the desktop to authenticate. The idea is that if someone got control of your computer, they'd have control of the places it goes. Requiring a second factor entirely like a phone seems safer. I think, if they have control of my computer, the game is over. Perhaps if they stole my computer, it might be better to have a second factor, but, they'd still have to break into KeePass to get to my sites. Given the strength of my password, it would be a tough race between them breaking my password and the end of the universe. I'm not worried. I prefer the added convenience.
Using KeePass for TOTP
[Revised March 26, 2024]
Since you've never set up a custom OTP field yet, you have to create your first one. You'll get a screen that looks like this:
The kind of OTP most people want is Time-Based, so choose that tab. So far, all of those I've encountered with Amazon, Dropbox, Google, MyChart and others were all Base32 with 6-digit codes being generated every 30 seconds using the HMAC-SHA-1 Algorithm. So, you can leave those alone and they'll be selected properly for you. However, you must enter the shared secret the site gave you. If you just got a QR Code, that is the code that displays the actual password. Use your phone's camera or QR code reader to determine the actual shared secret. I suggest recording the password and forgetting about the QR code. Enter your pre-shared password in the box.
Those passwords are sometimes displayed with spaces, like this:
The First One
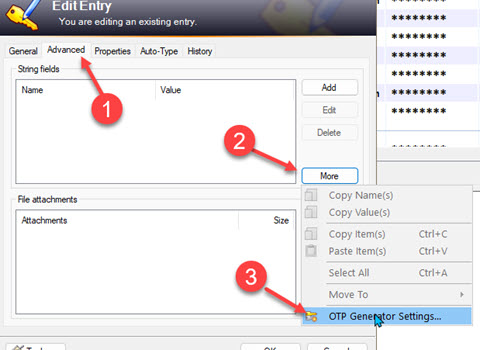
KeePass can handle most Time-based One-Time Passwords (TOTP) natively. You just need to add a custom field to that site's entry. Open the entry and click the Advanced tab (1). Then click More (2). Then select OTP Generator Settings (3).
Since you've never set up a custom OTP field yet, you have to create your first one. You'll get a screen that looks like this:

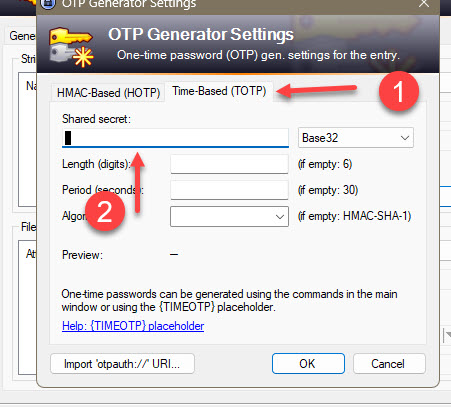
The kind of OTP most people want is Time-Based, so choose that tab. So far, all of those I've encountered with Amazon, Dropbox, Google, MyChart and others were all Base32 with 6-digit codes being generated every 30 seconds using the HMAC-SHA-1 Algorithm. So, you can leave those alone and they'll be selected properly for you. However, you must enter the shared secret the site gave you. If you just got a QR Code, that is the code that displays the actual password. Use your phone's camera or QR code reader to determine the actual shared secret. I suggest recording the password and forgetting about the QR code. Enter your pre-shared password in the box.
Those passwords are sometimes displayed with spaces, like this:
ALSD KD34 IOB8 3837 29KI
with spaces every 4 or 5 characters. If that's the case, you'll need to remove the spaces. They are not part of the password or shared secret.
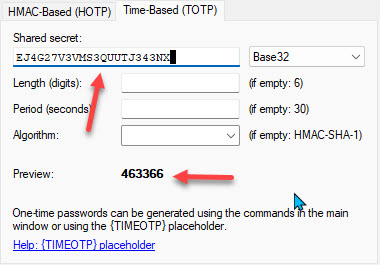
If you have a correctly formatted Shared Secret, it'll show in the space without red highlighting and the preview TOTP will be displayed, and change every 30 seconds. It'll look something like this that I made up with a fake Shared Secret.
Then, just click OK and you are done.
Now that you have created a custom field with a name and value, you can simply click Add instead of More.
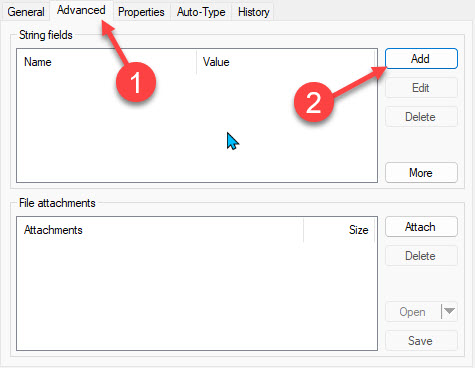
Now you pull down the name for the advanced field and choose TimeOtp-Secret-Base32.
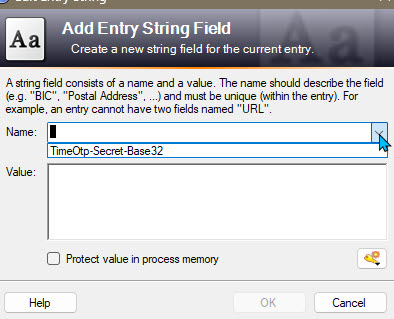
Then paste your shared secret password into the value field. NOTE! Be sure and remove any spaces in the code. They are there to help you type it, but KeePass will not remove them and they will break it.
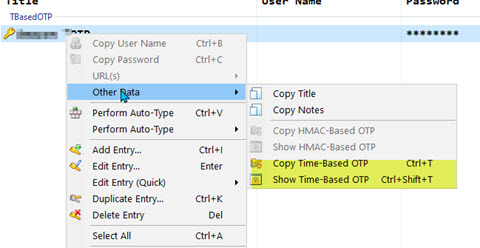
That's it. To use it, just right-click on the entry, select Other Data and select either view or copy the generated TOTP. You can also copy it with Ctrl-t or view it with Ctrl-Shift-t.
So far, every site I've had uses the Base 32 encryption.
If you have a correctly formatted Shared Secret, it'll show in the space without red highlighting and the preview TOTP will be displayed, and change every 30 seconds. It'll look something like this that I made up with a fake Shared Secret.

Then, just click OK and you are done.
After the first one
Now that you have created a custom field with a name and value, you can simply click Add instead of More.

Now you pull down the name for the advanced field and choose TimeOtp-Secret-Base32.

Then paste your shared secret password into the value field. NOTE! Be sure and remove any spaces in the code. They are there to help you type it, but KeePass will not remove them and they will break it.
That's it. To use it, just right-click on the entry, select Other Data and select either view or copy the generated TOTP. You can also copy it with Ctrl-t or view it with Ctrl-Shift-t.

So far, every site I've had uses the Base 32 encryption.
Use Bitwarden for TOTP
Bitwarden also offers TOTP creation for their premium accounts. These are only $10/year, and it is good to support a great product like Bitwarden. I don't have BitWarden, but I've heard it works well. Here is their description.Warning
You may hear that you shouldn't maintain your TOTP in the same program that holds your regular passwords. This defeats the idea of two separate factors. It is true that a separate second factor is better than not having a separate second factor. However, it is also more cumbersome. If your password is sufficiently difficult, it shouldn't be a problem. However, I use 2FAS on Android for my phone and tablet. If they could break the passwords at the website, then having the authenticator solves the possible data loss for you. I'm comfortable they can't gain access to MY password safe. But, keeping them completely separate, for instance, using 2FAS on Android and using your phone's 2-factor authentication app on Windows would be even more secure.Date: March 2024

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.