
Keeping clients' computers safe and profitable for over 30 years
Home Forms About Current Newsletter subscribe
Search All Articles
Browse by Category

Layered Security for 2021
Article for: Everyone
Difficulty: Hard
Importance: Critical
Difficulty: Hard
Importance: Critical
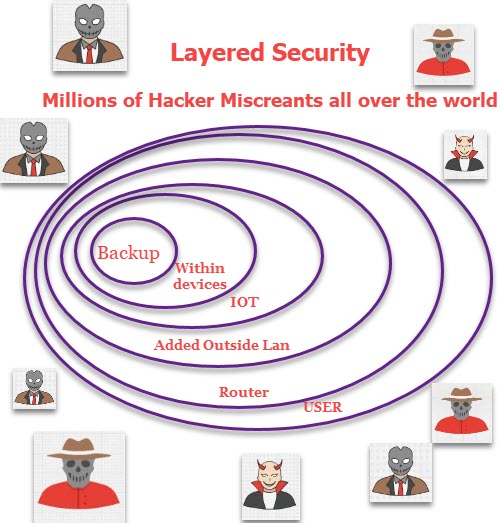
Protecting yourself and your office or home from Internet miscreants requires a multi-level approach. There is no simple silver bullet. I will explain multiple layers of risk management.
The user
You can be weakest or strongest link. Are you alert and practicing safe driving? Or are you racing down a 40 mph street at 90 mph while talking on your cell phone and eating a donut?
- Be careful what you do and where you go.
- Do not click on links to banks or other vendors' accounts. Use your password safe or browser bookmarks.
- Buy nothing from an unknown company’s advertisement. If it seems neat, find it from a known reliable vendor.
- Never buy from an email sent from an unsolicited source.
- Use a password safe for individual complex passwords for all sites. Do not use the same password on multiple sites.
Your Router
Your router is the wall between your computers and 100 million miscreants. A router blocks all attempts to get inside your computers unless they were invited in. If it has an unpatched flaw, or isn't setup properly, then it will fail, but basically, hackers, like vampires, can't come in unless invited. Attacks normally sneak in with something you allowed in.
- Be sure you are keeping your router patched. Your router should be patched at least twice a year. If it has been a year since it was updated, either update or replace. When you replace your router, get one that updates itself automatically.
- Have a reasonable password for access. Be sure you know how to access your router to set a new password or check its security or firmware updates. ISPs like Comcast keep their routers updated. If you rent your router, don’t worry about it being updated.
- Disable WPS, remote access and UPnP.
- Configure it to use a protective DNS service.
- Have separate guest and office Wi-Fi access
- Advanced routers can offer even greater protection and more firewall options.
An additional layer of external protection
Besides all the above, you can add another layer of protection.
- A SonicWall or similar firewall appliance
- A really advanced configurable business level router like the Ubiquity Dream Machine.
- NextDns, AdGuard, or similar system to block trackers and advertising and other dangers.
IOT Devices
Devices like cameras, doorbells and lights that connect to the Internet provide an additional source of danger. Miscreants often attack your computers through them.
- Only buy from established firms that have a record of updating their products when security flaws are found. I know it is tempting to get the cheaper cameras or doorbells, but don't. There will be security flaws. Vendors must patch their products. Cheap products don't get patched.
- Connect your devices (including smart TV or Roku) to a separate network. This will normally be a guest network. Newer business grade routers give us the ability to set up isolated networks even at home.
Protection within your devices
Each device can create a problem, so you need to protect them all.
- Use secure filtered protected DNS on all your devices.
- Keep your devices updated.
- Keep your software updated, particularly any the touch the Internet. I recommend Ninite Updater and PatchMyPC for Windows users.
- All Windows computers should have up-to-date antivirus. Depending on how your devices are used, this might be important for mobile devices as well.
- Your browser should have ad blocking because Ads sometimes contain viruses. If you care about privacy, then add tracking protection.
Backup
- Image backups will allow you to reset your computer to an earlier point in time. If you got attacked, you could simply return your computer to before the attack. The paid versions of Macrium offer to lock your images so attackers cannot encrypt them.
- Data Backups will allow you to recover lost data. But, ransomware will encrypt everything on any drive it can access. That will include data backups or images to USB drives or even network shares.
- Off-site backups like Spideroak One are secure from a ransomware attack since they do not have access via a networked drive letter.
- The basic rule for important files is 3 2 1. That is 3 copies of important files on at least 2 different devices with at least 1 off-site. To this, I also recommend periodic images.
Date: January 2021

This article is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.